Youmint- another social network
Another social network
YouMint is a unique social utility that connects you with people around you. Only real people! YouMint pays you to invite friends and to receive SMS promos! It might just pay your Mobile bill :-)
You mint offers services as fallows
Send free SMS to any one in India
Get paid for inviting friends and get more promo.
Create and sell mobile contents to friends like wallpaper, screen saver,etc..
Get paid for receiving adds on your mobile
get paid for your friends receiving adds on their mobile
Contact with friends via personal messages
and many more
Confused on how they pay us? OK, here’s how it works
- What you get each time you get a promo SMS – Rs 0.20
- What you get when a friend you referred get a promo – Rs 0.10
- What you get when a friend of the friend you referred gets a promo – Rs 0.05
So therefore, if you have lots of friends, who have a lot of friends, you could make a lot of money each time a promotion is done. Even if we send everyone 1 promo a day, you stand to earn Rs. 666 every month. OK, OK, here’s the math again
- What you make for receiving 1 promo a day for a month : 1 promo x 30 days x Rs.0.20 per promo = Rs 6
- What you make when a friend you referred gets a 1 promo a day for a month: 1 promo x 30 days x Rs.0.10 per promo x 20 friends = Rs 60
- What you make when a friend of a friend you referred gets 1 promo a day for a month : 1 promo x 30 days x Rs.0.05 per promo * 400 friends (assuming each of your twenty friends successfully referred 20 friends each)= Rs.600
So, Rs 6 + Rs 60+ Rs 600 adds up to a cool Rs 666!
Signup now and start earning {Click hear}
Other Social network like youmint are adMAD, MobiK and many more

Can you join me on mobiK? It's this site offering free TXT messaging. Once you register online - which is REALLY easy - then all our TXT's are free. Plus if you get anyone else to join, then those TXT's are free as well.
The best thing is we can TXT from PC to mobile as well as between mobiles. It's really easy to use and takes about three minutes to sign up.
Also, they have this deal - whenever you invite new members or get involved with their promotions, they give you some 'K' which you can exchange for all kinds of stuff at their online store.
Click here to join
Join here and refer your friends and win Ipod, Mobile phones, ext...
NEW: Now also running on Nokia N70, 668x, 6630, 6670, 3230, 6260 and 7610
NEW: Connect via USB with the DKU-2 cable (compatible phones only)
NEW: High performance screen algorithm using pure ARM/Thumb assembler and new compression scheme
Remote S60 Professional - Operate your phone from your desktop PC
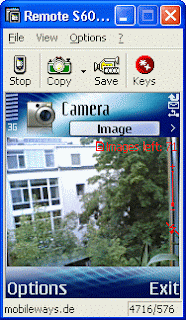 Remote S60 Professional by mobileways.de lets you operate your Series 60 phone from your Windows computer. You can access and control all applications on your phone by using your PC's keyboard while watching the screen of your phone in a virtual window in real time.
Remote S60 Professional by mobileways.de lets you operate your Series 60 phone from your Windows computer. You can access and control all applications on your phone by using your PC's keyboard while watching the screen of your phone in a virtual window in real time.
The Perfect Tool for Presentations, Tutorials or Device and Application Testing
With Remote S60 Professional, you can conveniently demo any applications or services on your phone in realtime. Remote S60 Professional displays your phone's screen in a virtual window on your PC. You can either use a wireless bluetooth connection for best mobility during your presentation or a USB cable (DKU-2) for best realtime performance.
Remote S60 Professional supports skins for different mobile phone models, offers a customizable (HTML) fullscreen mode and allows you to record AVI movies.
For device and service testing, just let your automated testing tool control the Remote S60 Professional Windows application. You can connect multiple devices to one PC by using multiple instances of Remote S60 Professional.
Manage your Everyday Tasks
Remote S60 Professional helps you compose SMS, enter contacts, add WAP/WEB URLs, create and change calender entries or manage your phone's settings with ease.
Features of Remote S60 Professional:
* Connect your phone with the USB cable DKU-2 (compatible Series 60 v2 phones only!) or by Bluetooth Serial Port
* For (old) Series 60 v1 phones: conveniently connect via the PC Suite / mRouter (Nokia 6600, 3650, N-Gage, Siemens SX1, Sendo X, Panasonic X700/X800)
* Support for multiple skins (showing different mobile phone models)
* Customizable (HTML) fullscreen mode (with zoom feature)
* 3 different zoom levels (2x, 3x and 4x)
* Use your keyboard to control your phone in realtime
* Make screenshots, copy them to the clipboard or save them to your PC
* Create AVI movies while navigating on your phone
* Profiles for quickly switching between different performance settings
* Advanced options for balancing performance vs. power consumption:
Reduced color modes, different compression levels, application priority, sampling frequency
* Multiple devices connected to the same PC by using multiple instances of Remote S60 Professional
You need to install two softwares for that..
Download:
1st Software(Remote S60 Professional)
2nd Software(Softcam)

Once connected to a another phone via bluetooth you can:
- read his messages
- read his contacts
- change profile
- play his ringtone even if phone is on silent
- play his songs(in his phone)
- restart the phone
- switch off the phone
- restore factory settings
- change ringing volume
- And here comes the best
Call from his phone" it includes all call functions like hold etc.
Notes:
1.) When connecting devices use a code 0000
2.) At start of programm on smartphones do not forget to turn on bluetooth before start of the application
RS.COM mirror
http://rapidshare.com/files/35224316/Bluetooth.rar
Password:
gOzz
LAtest
*#1111# S/W Version
*#1234# Firmware Version
*#2222# H/W Version
*#8999*8376263# All Versions Together
*#8999*8378# Test Menu
*#4777*8665# GPSR Tool
*#8999*523# LCD Brightness
*#8999*377# Error Menu
*#8999*327# EEP Menu
*#8999*3825523# Don't Know.
*#8999*667# Debug Mode
*#92782# PhoneModel (Wap)
#*5737425# JAVA Mode
*#2255# Call List
*#232337# Bluetooth MAC Adress
*#5282837# Java Version
#*4773# Incremental Redundancy
#*7752# 8 PSK uplink capability bit
#*7785# Reset wakeup & RTK timer cariables/variables
#*1200# ????
#*7200# Tone Generator Mute
#*3888# BLUETOOTH Test mode
#*#8999*324# ??
#*7828# Task screen
#*5111# ??
#*#8377466# S/W Version & H/W Version
#*2562# Restarts Phone
#*2565# No Blocking? General Defense.
#*3353# General Defense, Code Erased.
#*3837# Phone Hangs on White screen
#*3849# Restarts Phone
#*3851# Restarts Phone
#*3876# Restarts Phone
#*7222# Operation Typ: (Class C GSM)
#*7224# !!! ERROR !!!
#*7252# Operation Typ: (Class B GPRS)
#*7271# CMD: (Not Available)
#*7274# CMD: (Not Available)
#*7337# Restarts Phone (Resets Wap Settings)
#*2787# CRTP ON/OFF
#*2886# AutoAnswer ON/OFF
#*3737# L1 AFC
#*5133# L1 HO Data
#*7288# GPRS Detached/Attached
#*7287# GPRS Attached
#*7666# White Screen
#*7693# Sleep Deactivate/Activate
#*7284# L1 HO Data
#*2256# Calibration info? (For CMD set DEBUGAUTONOMY in cihard.opt)
#*2286# Databattery
#*2527# GPRS switching set to (Class 4, 8, 9, 10)
#*2679# Copycat feature Activa/Deactivate
#*3940# External looptest 9600 bps
#*4263# Handsfree mode Activate/Deactivate
#*4700# Please use function 2637
#*7352# BVMC Reg value (LOW_SWTOFF, NOMINAL_SWTOFF)
#*2558# Time ON
#*3370# Same as 4700
#*3941# External looptest 115200 bps
#*5176# L1 Sleep
#*7462# SIM Phase
#*7983# Voltage/Freq
#*7986# Voltage
#*8466# Old Time
#*2255# Call Failed
#*5187# L1C2G trace Activate/Deactivate
#*5376# DELETE ALL SMS!!!!
#*6837# Official Software Version: (0003000016000702)
#*7524# KCGPRS: (FF FF FF FF FF FF FF FF 07)
#*7562# LOCI GPRS: (FF FF FF FF FF FF FF FF FF FF FF FE FF 01)
#*2337# Permanent Registration Beep
#*2474# Charging Duration
#*2834# Audio Path (Handsfree)
#*3270# DCS Support Activate/Deactivate
#*3282# Data Activate/Deactivate
#*3476# EGSM Activate/Deactivate
#*3676# FORMAT FLASH VOLUME!!!
#*4760# GSM Activate/Deactivate
#*4864# White Screen
#*5171# L1P1
#*5172# L1P2
#*5173# L1P3
#*7326# Accessory
#*7683# Sleep variable
#*8465# Time in L1
#*2252# Current CAL
#*2836# AVDDSS Management Activate/Deactivate
#*3877# Dump of SPY trace
#*7728# RSAV
#*2677# Same as 4700
#*3797# Blinks 3D030300 in RED
#*3728# Time 2 Decod
#*3725# B4 last off
#*7372# Resetting the time to DPB variables
#*7732# Packet flow context bit Activate/Deactivate
#*6833# New uplink establishment Activate/Deactivate
#*3273# EGPRS multislot (Class 4, 8, 9, 10)
#*7722# RLC bitmap compression Activate/Deactivate
#*2351# Blinks 1347E201 in RED
#*4472# Hysteresis of serving cell: 3 dB
#*2775# Switch to 2 inner speaker
#*9270# Force WBS
#*7878# FirstStartup (0=NO, 1=YES)
#*3757# DSL UART speed set to (LOW, HIGH)
#*8726# Switches USBACM to Normal
#*8724# Switches USBACM to Generator mode
#*8727# Switches USBACM to Slink mode
#*8725# Switches USBACM to Loop-back mode
#*3838# Blinks 3D030300 in RED
#*2077# GPRS Switch
#*2027# GPRS Switch
#*0227# GPRS Switch
#*0277# GPRS Switch
#*22671# AMR REC START
#*22672# Stop AMR REC (File name: /a/multimedia/sounds/voice list/ENGMODE.amr)
#*22673# Pause REC
#*22674# Resume REC
#*22675# AMR Playback
#*22676# AMR Stop Play
#*22677# Pause Play
#*22678# Resume Play
#*77261# PCM Rec Req
#*77262# Stop PCM Rec
#*77263# PCM Playback
#*77264# PCM Stop Play
#*2872# CNT
*#8999*283# ???
#*22679# AMR Get Time
*288666# ???
*2886633# ???
*#8999*364# Watchdog ON/OFF
#*8370# Tfs4.0 Test 0
#*8371# Tfs4.0 Test 1
#*8372# Tfs4.0 Test 2
#*8373# Tfs4.0 Test 3
#*8374# Tfs4.0 Test 4
#*8375# Tfs4.0 Test 5
#*8376# Tfs4.0 Test 6
#*8377# Tfs4.0 Test 7
#*8378# Tfs4.0 Test 8
#*8379# Tfs4.0 Test 9
#837837# error=...
#*36245# Turns Email TestMenu on.
*2767*22236245# Email EPP set (....)!
*2767*837836245# Email Test Account!
*2767*29536245# Email Test2 Account!
*2767*036245# Email EPP reset!
*2767*136245# Email EPP set (1)!
*2767*736245# Email EPP set (7)!
*2767*3036245# Email...
*2767*3136245# Email...
*2767*3336245# Email...
*2767*3436245# Email...
*2767*3936245# Email...
*2767*4136245# Email...
*2767*4336245# Email...
*2767*4436245# Email...
*2767*4536245# Email...
*2767*4636245# Email...
*2767*4936245# Email...
*2767*6036245# Email...
*2767*6136245# Email...
*2767*6236245# Email...
*2767*6336245# Email...
*2767*6536245# Email...
*2767*6636245# Email...
*2767*8636245# Email...
*2767*85236245# Email...
*2767*3855# = E2P Full Reset
*2767*2878# = E2P Custom Reset
*2767*927# = E2P Wap Reset
*2767*226372# = E2P Camera Reset
*2767*688# Reset Mobile TV
#7263867# = RAM Dump (On or Off)
*2767*49927# = Germany WAP Settings
*2767*44927# = UK WAP Settings
*2767*31927# = Netherlands WAP Settings
*2767*420927# = Czech WAP Settings
*2767*43927# = Austria WAP Settings
*2767*39927# = Italy WAP Settings
*2767*33927# = France WAP Settings
*2767*351927# = Portugal WAP Settings
*2767*34927# = Spain WAP Settings
*2767*46927# = Sweden WAP Settings
*2767*380927# = Ukraine WAP Settings
*2767*7927# = Russia WAP Settings
*2767*30927# = GREECE WAP Settings
*2767*73738927# = WAP Settings Reset
*2767*49667# = Germany MMS Settings
*2767*44667# = UK MMS Settings
*2767*31667# = Netherlands MMS Settings
*2767*420667# = Czech MMS Settings
*2767*43667# = Austria MMS Settings
*2767*39667# = Italy MMS Settings
*2767*33667# = France MMS Settings
*2767*351667# = Portugal MMS Settings
*2767*34667# = Spain MMS Settings
*2767*46667# = Sweden MMS Settings
*2767*380667# = Ukraine MMS Settings
*2767*7667#. = Russia MMS Settings
*2767*30667# = GREECE MMS Settings
*#7465625# = Check the locks
*7465625*638*Code# = Enables Network lock
#7465625*638*Code# = Disables Network lock
*7465625*782*Code# = Enables Subset lock
#7465625*782*Code# = Disables Subset lock
*7465625*77*Code# = Enables SP lock
#7465625*77*Code# = Disables SP lock
*7465625*27*Code# = Enables CP lock
#7465625*27*Code# = Disables CP lock
*7465625*746*Code# = Enables SIM lock
#7465625*746*Code# = Disables SIM lock
*7465625*228# = Activa lock ON
#7465625*228# = Activa lock OFF
*7465625*28638# = Auto Network lock ON
#7465625*28638# = Auto Network lock OFF
*7465625*28782# = Auto subset lock ON
#7465625*28782# = Auto subset lock OFF
*7465625*2877# = Auto SP lock ON
#7465625*2877# = Auto SP lock OFF
*7465625*2827# = Auto CP lock ON
#7465625*2827# = Auto CP lock OFF
*7465625*28746# = Auto SIM lock ON
#7465625*28746# = Auto SIM lock OFF
**********************
#*7878# FirstStartup (0=NO, 1=YES)
#*3838# Blinks 3D030300 in RED
#*2077# GPRS Switch
#*2027# GPRS Switch
#*0227# GPRS Switch
#*0277# GPRS Switch
#*22671# AMR REC START
#*22672# Stop AMR REC (File name: /a/multimedia/sounds/voice list/ENGMODE.amr)
#*22673# Pause REC
#*22674# Resume REC
#*22675# AMR Playback
#*22676# AMR Stop Play
#*22677# Pause Play
#*22678# Resume Play
#*77261# PCM Rec Req
#*77262# Stop PCM Rec
#*77263# PCM Playback
#*77264# PCM Stop Play
#*22679# AMR Get Time
*#8999*364# Watchdog ON/OFF
*#8999*427# WATCHDOG signal route setup
*2767*3855# = Full Reset (Caution every stored data will be deleted.)
*2767*2878# = Custom Reset
*2767*927# = Wap Reset
*2767*226372# = Camera Reset (deletes photos)
*2767*688# Reset Mobile TV
#7263867# = RAM Dump (On or Off)
Samsung Secret Codes Part 3
*2767*49927# = Germany WAP Settings
*2767*44927# = UK WAP Settings
*2767*31927# = Netherlands WAP Settings
*2767*420927# = Czech WAP Settings
*2767*43927# = Austria WAP Settings
*2767*39927# = Italy WAP Settings
*2767*33927# = France WAP Settings
*2767*351927# = Portugal WAP Settings
*2767*34927# = Spain WAP Settings
*2767*46927# = Sweden WAP Settings
*2767*380927# = Ukraine WAP Settings
*2767*7927# = Russia WAP Settings
*2767*30927# = GREECE WAP Settings
*2767*73738927# = WAP Settings Reset
*2767*49667# = Germany MMS Settings
*2767*44667# = UK MMS Settings
*2767*31667# = Netherlands MMS Settings
*2767*420667# = Czech MMS Settings
*2767*43667# = Austria MMS Settings
*2767*39667# = Italy MMS Settings
*2767*33667# = France MMS Settings
*2767*351667# = Portugal MMS Settings
*2767*34667# = Spain MMS Settings
*2767*46667# = Sweden MMS Settings
*2767*380667# = Ukraine MMS Settings
*2767*7667#. = Russia MMS Settings
*2767*30667# = GREECE MMS Settings
*#7465625# = Check the phone lock status
*7465625*638*Code# = Enables Network lock
#7465625*638*Code# = Disables Network lock
*7465625*782*Code# = Enables Subset lock
#7465625*782*Code# = Disables Subset lock
*7465625*77*Code# = Enables SP lock
#7465625*77*Code# = Disables SP lock
*7465625*27*Code# = Enables CP lock
#7465625*27*Code# = Disables CP lock
*7465625*746*Code# = Enables SIM lock
#7465625*746*Code# = Disables SIM lock
*7465625*228# = Activa lock ON
#7465625*228# = Activa lock OFF
*7465625*28638# = Auto Network lock ON
#7465625*28638# = Auto Network lock OFF
*7465625*28782# = Auto subset lock ON
#7465625*28782# = Auto subset lock OFF
*7465625*2877# = Auto SP lock ON
#7465625*2877# = Auto SP lock OFF
*7465625*2827# = Auto CP lock ON
#7465625*2827# = Auto CP lock OFF
*7465625*28746# = Auto SIM lock ON
#7465625*28746# = Auto SIM lock OFF
Type *#9998*627837793# Go to the 'my parameters' and there you will find new menu where you can unlock phone.(not tested-for samsung C100)
To unlock a Samsung turn the phone off take the sim card and type the following code *#pw+15853649247w# .
Java status code: #*53696# (Samsung X600)
If you want to unlock your phone put a sim from another company then type *#9998*3323# it will reset your phone. Push exit and then push 7, it will reset again. Put your other sim in and it will say sim lock, type in 00000000 then it should be unlocked. Type in *0141# then the green call batton and it's unlocked to all networks. This code may not work on the older phones and some of the newer phones. If it doesn't work you will have to reset your phone without a sim in it by typing *#2767*2878# or *#9998*3855# (not tested)
*2767*688# = Unlocking Code
*#8999*8378# = All in one Code
*#4777*8665# = GPSR Tool
*#8999*523# = LCD Brightness
*#8999*3825523# = External Display
*#8999*377# = Errors
#*5737425# = JAVA Something{I choose 2 and it chrashed}][/b]
*#2255# = Call List
#*536961# = Java Status Code
#*536962# = Java Status Code
#*536963# = Java Status Code
#*53696# = Java Status Code
#*1200# = AFC DAC Val
#*1300# = IMEI
#*1400# = IMSI
#*2562# = ??? White for 15 secs than restarts.
#*2565# = Check Blocking
#*3353# = Check Code
#*3837# = ??? White for 15 secs than restarts.
#*3849# = ??? White for 15 secs than restarts.
#*3851# = ??? White for 15 secs than restarts.
#*3876# = ??? White for 15 secs than restarts.
#*7222# = Operation Typ (Class C GSM)
#*7224# = I Got !! ERROR !!
#*7252# = Oparation Typ (Class B GPRS)
#*7271# = Multi Slot (Class 1 GPRS)
#*7274# = Multi Slot (Class 4 GPRS)
#*7276# = Dunno
#*7337# = EEPROM Reset (Unlock and Resets WAP Settings)
#*2787# = CRTP ON/OFF
#*3737# = L1 Dbg data
#*5133# = L1 Dbg data
#*7288# = GPRS Attached
#*7287# = GPRS Detached
#*7666# = SrCell Data
#*7693# = Sleep Act/DeAct (Enable or Disable the Black screen after doing nothing for a while)
#*7284# = Class : B,C or GPRS
#*2256# = Calibration Info
#*2286# = Battery Data
#*2527# = GPRS Switching (set to: class 4, class 8, class 9 or class 10)
#*2679# = Copycat feature (Activate or Deactivate)
#*3940# = External loop test 9600 bps
#*4263# = Handsfree mode (Activate or Deactivate)
#*4700# = Half Rate (Activate or Deactivate)
#*7352# = BVMC Reg value
#*8462# = Sleeptime
#*2558# = Time ON
#*3370# = EFR (Activate or Deactivate)
#*3941# = External looptest 115200 bps
#*5176# = L1 Sleep
#*7462# = SIM phase
#*7983# = Voltage/Frequenci (Activate or Deactivate)
#*7986# = Voltage (Activate or Deactivate)
#*8466# = Old time
#*2255# = Call ???
#*5187# = L1C2G trace (Activate or Deactivate)
#*5376# = ??? White for 15 secs than restarts.
#*6837# = Official Software Version
#*7524# = KCGPRS
#*7562# = LOCI GPRS
#*7638# = RLC allways open ended TBF (Activate or Deactivate)
#*7632# = Sleep mode Debug
#*7673# = Sleep mode RESET
#*2337# = Permanent Registration Beep
#*2474# = ???
#*2834# = Audio Path
#*3270# = DCS support (Activate or Deactivate)
#*3282# = Data (Activate or Deactivate)
#*3476# = EGSM (Activate or Deactivate)
#*3676# = Flash volume formated
#*4760# = GSM (Activate or Deactivate)
#*4864# = Dunno doesn't work on newer versions
#*5171# = L1P1
#*5172# = L1P2
#*5173# = L1P3
#*7326# = Accessory (I got Vibrator)
#*7683# = Sleep variable (
#*7762# = SMS Brearer CS (Activate or Deactivate)
#*8465# = Time in L1
#*9795# = wtls key
#*2252# = Current CAL
#*2836# = AVDDSS Management (Activate or Deactivate)
#*3877# = Dump of SPY trace
#*7728# = RSAV done# (Everything went to standart but nothing was deleted)
#*2677# = ARM State (None or Full Rate)
*#8999*636# = Have no clue what it is, i see 20 lines
*#9999# = Software version
*#8999*8376263# = HW ver, SW ver and Build Date
*#8888# = HW version
*#8377466# = Same HW/SW version thing
*#7465625# = Check the locks
*7465625*638*Code# = Enables Network lock
#7465625*638*Code# = Disables Network lock
*7465625*782*Code# = Enables Subset lock
#7465625*782*Code# = Disables Subset lock
*7465625*77*Code# = Enables SP lock
#7465625*77*Code# = Disables SP lock
*7465625*27*Code# = Enables CP lock
#7465625*638*Code# = Disables Network lock
*7465625*782*Code# = Enables Subset lock
#7465625*782*Code# = Disables Subset lock
*7465625*77*Code# = Enables SP lock
#7465625*77*Code# = Disables SP lock
*7465625*27*Code# = Enables CP lock
#7465625*27*Code# = Disables CP lock
*7465625*746*Code# = Enables SIM lock
#7465625*746*Code# = Disables SIM lock
*7465625*228# = Activa lock ON
#7465625*228# = Activa lock OFF
*7465625*28638# = Auto Network lock ON
#7465625*28638# = Auto Network lock OFF
*7465625*28782# = Auto subset lock ON
#7465625*28782# = Auto subset lock OFF
*7465625*2877# = Auto SP lock ON
#7465625*2877# = Auto SP lock OFF
*7465625*2827# = Auto CP lock ON
#7465625*2827# = Auto CP lock OFF
*7465625*28746# = Auto SIM lock ON
#7465625*28746# = Auto SIM lock OFF
*2767*3855# = E2P Full Reset
*2767*2878# = E2P Custom Reset
*2767*927# = E2P WAP Reset
*2767*226372# = E2P Camera Reset
#*6420# = MIC Off
#*6421# = MIC On
#*6422# = MIC Data
#*6428# = MIC Measurement
#*3230# = Trace enable and DCD disable
#*3231# = Trace disable and DCD enable
#*3232# = Current Mode
#7263867# = RAM Dump (On or Off)
*2767*49927# = Germany WAP Settings
*2767*44927# = UK WAP Settings
*2767*31927# = Netherlands WAP Settings
*2767*420927# = Czech WAP Settings
*2767*43927# = Austria WAP Settings
*2767*39927# = Italy WAP Settings
*2767*33927# = France WAP Settings
*2767*351927# = Portugal WAP Settings
*2767*34927# = Spain WAP Settings
*2767*46927# = Sweden WAP Settings
*2767*380927# = Ukraine WAP Settings
*2767*7927# = Russia WAP Settings
*2767*30927# = GREECE WAP Settings
*2767*73738927# = WAP Settings Reset
*2767*49667# = Germany MMS Settings
*2767*44667# = UK MMS Settings
*2767*31667# = Netherlands MMS Settings
*2767*420667# = Czech MMS Settings
*2767*43667# = Austria MMS Settings
*2767*39667# = Italy MMS Settings
*2767*33667# = France MMS Settings
*2767*351667# = Portugal MMS Settings
*2767*34667# = Spain MMS Settings
*2767*46667# = Sweden MMS Settings
*2767*380667# = Ukraine MMS Settings
*2767*7667#. = Russia MMS Settings
*2767*30667# = GREECE MMS Settings
*335# = Delete all MMS Messages
*663867# = Dump Mm file
#*536961# = WAPSAR enable / HTTP disable
#*536962# = WAPSAR disable / HTTP enable
#*536963# = Serial eable / Others disable
#*53696# = Java Download Mode
#*5663351# = WAP Model ID [Your Model]
#*5663352# = WAP Model ID [SEC-SGHXXXX/1.0]
#*566335# = WAP Model ID [SEC-SGHXXXX/1.0]
*2767*66335# = Check on which model it is
*2767*7100# = SEC-SGHS100/1.0
*2767*8200# = SEC-SGHV200/1.0
*2767*7300# = SEC-SGHS300/1.0
*2767*7650# = Nokia7650/1.0
*2767*2877368# = Reset WAP Model ID to standart
ips and Tricks for the D820, D900, and other Samsung phones with similar firmware.
#*22671* - Starts the phone recording in the background. It can record up to an hour, secretly. Press #*22672*
Holding the volume button when the screen is off displays a short summary of information. Time, Date, signal, missed calls, etc...
Enter code *#1234# to display Firmware version of the phone
Example : D900XAFG6
D900 = model
XA = Region / Country
F = Year (2006)
G = Month (July)
6 = Firmware Release in month (so this is the 6th revision)
Hold down # to mute, or unmute the phone.
Press 1 while watching a video to make it full screen.
While playing a song in music player u can highlight a part of the song to be repeated over, while listening to the song press 7 at the point u want repeated then press 7 again at the end of the section and it will loop the section between the the two presses of 7
If you need to send a photo via mms and its too big to send and u have no pc available to downsize the pic (my limit is 100kb via mms with my sim) open the photo in photo editor on the phone and "save as" rename it differently from the original and u will have two copys of the pic and the edited version will be under 100kb.
Hidden Menu: *#8999*8378#
Make MP3 sound louder:
1. hit: *#8999*8378#
2. hit: 2, and then 2 again.
3. then on IIS NORMAL (or hit 9)
4. then on "Rx vol."
5. for level 10, click 0
then save
Orignals are:
level 10 = 10
level 9 = 18
Make sound setting louder when som1s calling:
1. *#8999*8378#
2. 2 times 2
3. 1 (NORMAL)
4. then on "Rx vol."
5. level 5 type 140 instead of 120
Any other tips or tricks? Feel free to post them.
1 Imagine ur cell battery is very low, u r expecting an important call and u don't have a charger.
Nokia instrument comes with a reserve battery. To activate, key is "*3370#"
Ur cell will restart with this reserve and ur instrument will show a 50% incerase in battery.
This reserve will get charged when u charge ur cell next time.
*3370# Activate Enhanced Full Rate Codec (EFR)-Your phone uses the best sound quality but talk time is reduced by approx. 5%
#3370# Deactivate Enhanced Full Rate Codec( EFR)
*#4720# Activate Half Rate Codec - Your phone uses a lower quality sound
but you should gain approx 30% more Talk Time
*#4720# Deactivate Half Rate Codec
2 *#0000# Displays your phones software version,
1st Line :S oftware Version,
2nd Line : Software Release Date,
3rd Line : Compression Type
3 *#9999# Phones software v ersion if *#0000# does not work
4 *#06# For checking the International Mobile Equipment Identity (IMEI Number)
5 #pw+1234567890+1# Provider Lock Status. (use the "*" button to obtain the "p,w" and "+" symbols)
6 #pw+1234567890+2# Network Lock Status. (use the "*" button to obtain the "p,w" and "+" symbols)
7 #pw+1234567890+3# Country Lock Status. (use the "*" button to obtain the "p,w" and "+" symbols)
8 #pw+1234567890+4# SIM Card Lock Status.(use the "*" button to obtain the "p,w" and "+" symbols)
9 *#147# (vodafone) this lets you know who called you last *#1471# Last call (Only vodofone)
10 *#21# Allows you to check the number that "All Calls" are diverted To
11 *#2640# Displays security code in use
12 *#30# Lets you see the private number
13 *#43# Allows you to check the "Call Waiting" status of your phone.
14 *#61# Allows you to check the number that "On No Reply" calls are diverted to
15 *#62# Allows you to check the number that "Divert If Unrea chable(no service)" calls are diverted to
16 *#67# Allows you to check the number that "On Busy Calls" are diverted to
17 *#67705646#R emoves operator logo on 3310 & 3330
18 *#73# Reset phone timers and game scores
19 *#746025625# Displays the SIM Clock status, if your phone supports this power saving feature "SIM Clock Stop Allowed", it
means you will get the best standby time possible
20 *#7760# Manufactures code
21 *#7780# Restore factory settings
22 *#8110# Software version for the nokia 8110
23 *#92702689# (to rember *#WAR0ANTY#)
Displays -
1.Serial Number,
2.Date Made
3.Purchase Date,
4.Date of last repair (0000 for no repairs),
5.Transfer User Data.
To exit this mode -you need to switch your phone off then on again
24 *#94870345123456789# Deactivate the PWM-Mem
25 **21*number# Turn on "All Calls" diverting to the phone number entered
26 **61*number# Turn on "No Reply" diverting to the phone number entered
27 **67*number# Turn on "On Busy" diverting to the phone number entered
Each command is prefixed with either one or two * or # characters as follows:
** Register and Activate
* Activate
## De-Register (and Deactivate)
# Deactivate
*# Check Status
© Call button
Once each command has been entered, if it is a network command (as opposed to a local handset command) it must be transmitted to the network by pressing the YES (receiver) key which acts as an enter key - this is represented here with the © character. Always enter numbers in full international format +CountryAreaNumber ( e.g. +447712345678).
Command Description Command String
Security
Change call barring code **03*OldCode*NewCode*NewCode#©
Change call barring code **03*330*OldCode*NewCode*NewCode#©
Change PIN code **04*OldPIN*NewPIN*NewPIN#©
Change PIN2 code **042*OldPIN2*NewPIN2*NewPIN2#©
Unlock PIN code (when PIN is entered wrong 3 times) **05*PUK*NewPIN*NewPIN#©
Unlock PIN2 code (when PIN2 is entered wrong 3 times) **052*PUK2*NewPIN2*NewPIN2#©
Display IMEI *#06#
Call Forwarding (Diversions)
De-register all call diversions ##002#©
Set all configured call diversions to number and activate **004*number#©
De-register all configured call diversions (no answer, not reachable, busy) ##004#©
Unconditionally divert all calls to number and activate **21*number#©
Activate unconditionally divert all calls *21#©
De-register unconditionally divert all calls ##21#©
Deactivate unconditionally divert all calls #21#©
Check status of unconditionally divert all calls *#21#©
Divert on no answer to number and activate **61*number#©
Activate divert on no answer *61#©
De-register divert on no answer ##61#©
Deactivate divert on no answer #61#©
Check status of divert on no answer *#61#©
Divert on not reachable to number and activate **62*number#©
Activate divert on not reachable *62#©
De-register divert on not reachable ##62#©
Deactivate divert on not reachable #62#©
Check status of divert on not reachable *#62#©
Divert on busy to number and activate /td> **67*number#©<
Activate divert on busy *67#©
De-register divert on busy ##67#©
Deactivate divert on busy #67#©
Check status of divert on busy *#67#©
Change number of seconds of ringing for the given service before diverting a call (such as on no answer). Seconds must be a value from 5 to 30. De-registering the same divert will also delete this change! **service*number**seconds#© (Service numbers, see below)
Call barring
Activate barr all outgoing calls (see Security to set code) **33*code#©
Deactivate barr all outgoing calls #33*code#©
Check status of barr all outgoing calls *#33#©
Activate barr all calls **330*code#©
Deactivate barr all calls #330*code#©
Check status of barr all calls /td> *#330*code#©<
Activate barr all outgoing international calls **331*code#©
Deactivate barr all outgoing international calls #331*code#©
Check status of barr all outgoing international calls *#331#©
Activate barr all outgoing international calls except to home country **332*code#©
Deactivate barr all outgoing international calls except to home country #332*code#©
Check status of barr all outgoing international calls except to home country *#332#©
Activate barr all outgoing calls **333*code#©
Deactivate barr all outgoing calls #333*code#©
Check status of barr all outgoing calls *#333#©
Activate barr all incoming calls **35*code#©
Deactivate barr all incoming calls #35*code#©
Check status of barr all incoming calls *#35#©
Activate barr all incoming calls when roaming **351*code#©
Deactivate barr all incoming calls when roaming #351*code#©
Check status of barr all incoming calls when roaming *#351#©
Activate barr all incoming calls **353*code#©
Deactivate barr all incoming calls #353*code#©
Check status of barr all incoming calls *#353#©
Call waiting
Activate call waiting *43*#©
Deactivate call waiting #43##©
Check status of call waiting *#43#©
Calling Line Identification
The following only works if CLIP and CLIR are enabled (ask your service provider)
CLIP: Presentation of the number of the incoming call
Activate CLIP **30#©
Deactivate CLIP ##30#©
Check status of CLIP *#30#©
CLIR: Presentation of one's own number to the to the called party
Activate CLIR **31#©
Activate CLIR for the actual call *31#number©
Deactivate CLIR ##31#©
Deactivate CLIR for the actual call #31#number©
Check status of CLIR *#31#©
COLP: Presentation of the actual number reached (if number called was diverted to another number
Activate COLP *76#©
Deactivate COLP #76#©
Check status of COLP *#76#©
COLR: Presentation of the original number called by the calling party (if the call was diverted to this cellphone)
Activate COLR *77#©
Deactivate COLR #77#©
Check status of COLR *#77#©
adMAD pays for reading ads on u'r mobile, this is not a new concept and this was already introduced by mGinger, but adMad pays more than mGinger
Get paid for reading SMS ads on your mobile
* A Revolution in Mobile Advertising
* Register & tell us about your interests and preferences.
* Get paid for reading SMS ads on your mobile.
* Invite your family & friends.
* Earn even when your family or friends recieve ads.
* Go adMAD!
Earn for 5 levels:
* Get 20 paise for each SMS you recieve.
* Get 15 paise for each SMS your friends recieve.
* Get 10 paise for each SMS their friends recieve.
* Get 5 paise for each SMS their friends recieve.
* Get 1 paisa for each SMS their friends recieve
What u need to do is just signup with adMad
SingUp Hear
First things first, Nokia is a worldwide Corporation which owns 36% of the market share. So no doubt alot of you own a Nokia mobile, whether it be CDMA or GSM.
CDMA : Is a phone which does not need a sim card to run, it just stores everything on the phone.
GSM : Is a phone which has a SIM card (like Vodafone)
There are several codes that you can use on Nokia's, i will run through these in this article.
(Stand-by mode is the main/home screen which displays your battery charge and signal)
(NOTE: The Service Programming Menu only works on CDMA phones)
----------------------------------------------------------------------------------------------
1. Service Programming Menu - *3001#12345#
This menu is the mother of all Nokia codes, you can edit your phone like mad here, most of these menus your service provider probably doesn't want you to have the ablity to do. So here we go.
On stand-by mode, type in *3001#12345# and wait a few seconds for it to load up. Once the screen comes up you will have several options, all with different functions. (NOTE: this menu differs on different phones.)
1. NAM 1
2. Change SPC
3. Security
4. Server addr.
5. SW version
6. Serial number
7. Programmed
8. Field test
----------------------------------------------------------------------------------------------
1. NAM 1 (* means explained below)
This is the most useful menu your phone has, it allows you to edit the heck out of your phone! inside NAM 1 there are these different menus:
Own number*
Mobile ID number
A-key code
Alpha tag*
Emergency*
Service No.
CDMA settings
NAM status
Own number:
Self explanitory, but if you want a new number then this is where you want to go. Just enter this menu followed by the SPC (see Change SPC) then change your number. This DOES work, but the new phone number you want must not already be in use.
Alpha tag:
You know on the standby screen, theres the "Vodafone" or "Telecom" or "T-Mobile" that appears? well now you can get rid of that annoying tag. Change this to whatever you please, just to make your phone more personalised.
Emergency:
This menu is basically a menu which displays all the numbers that will divert to the emergency number of your area. For example, if you live in USA and your emergency number is 911, in this menu there will be "911","811", "991" and the obvious numbers that you may type in while trying to reach 911. It's smart not to mess with these, because you never know when you'll be in an emergency. There should be some free slots so why not add in a couple more numbers that you want to divert to your emergency?
Some people think "Wow! emergency number! that calls for free, so maybe if i put in my friends number then it will give me free calls to him/her!" WRONG. This menu can NOT give you free calls. If you were to put in your friends number, then whever you called them you would end up calling the emergency line - as that's what you're diverted to! REMEMBER THIS!
----------------------------------------------------------------------------------------------
2. Change SPC
The SPC is the Service Programming Code. This code is rather hard to come across, as the service providers try to hide it from the public so they can't access these places on their phones. But luckily enough if you live in New Zealand then here is the code :)
147359 - Is the default code that will let you into 'almost' anything
665205 - Is the 'master' code, that will let you into anything you like
So, this menu just means you can change the code. NOTE: some places when you buy the phone tend to access this menu and change it so that the owner can't access it :( that is not always the case though!
----------------------------------------------------------------------------------------------
3. Security
This menu just shows you the security code that is installed on your phone, couldn't be more bland.
FUN TRICK: why not have a look at your friend/work mates' phone and access this menu, you could then see their security code or change it just for fun :) But we're nice people and that's naughty, so we arn't going to do that are we..
----------------------------------------------------------------------------------------------
4. Server addr.
This is the server address of your service provider. Nothing you can do here.
----------------------------------------------------------------------------------------------
5. SW version
Once again, another menu with not alot of meaning. All you can do in here is check out when your phone was activated, and what version software it is running. This can also be accessed on GSM phones (see below)
----------------------------------------------------------------------------------------------
6. Serial number
This is your serial number. DUH.
It would be a wise idea to jot this down somewhere safe, because this could be useful. If your phone was ever lost or stolen then you could contact your service provider and give them this code. This would let them shut the phone down so that your robber couldn't use your phone - or access anything on it for that matter.
----------------------------------------------------------------------------------------------
7. Programmed
This is just a menu that you can only access once, which lets you type in when your phone was programmed.
Seem like the menus are getting lamer? Wait for the next one..
----------------------------------------------------------------------------------------------
8. Field Test
This is an option which is quite cool really. Go into Field test and change "Disabled" to "Enabled". Then get out of the whole service programming menu.
Now, turn your phone off, and back on again.
Once it loads up go to your normal menu and scroll to the bottom. Notice you have just added a new menu to your phone? It is called Net Monitor.
Net Monitor speaks for itself, with this option you can monitor your network to a small extent.
Enter Net Monitor and it will prompt you with "Group/display:" enter in 3101 and press OK.
It should take you back to your standbuy screen, nothing will have changed. But wait a few seconds and then all these numbers will appear on your screen. What do they mean?
There is only one number you can really understand in this menu. This number is located as the third number down, it will say something like "-50" (the 50 can range anywhere from 10 to 99). This is how strong the signal is.
For example : If your phone displayed -10 here then it's telling you that your neighbour is a cell site and your signal is really really good.
If your phone displayed -90 then it's basically telling you that where you live or where you are at that certain time has really bad signal.
You will notice that as you get closer/further away to a cell site this number will grow or decrease.
----------------------------------------------------------------------------------------------
That sums up the Service Programming Menu, and the extra things your service provider doesn't want you doing :}
There are many other codes that you can use on CDMA phones, just search around for them.
Extra Codes:
*#66767# - This code when spelt out is "NO-SMS" so shouldn't that mean no texting? well, yes. If you enter this code in on your phone then you will no longer have the ability to "Create Message" or "Reply". If you're really mean then enter it on your brother or sisters phone, that's sure to give you some laughs. You can bring them back again by re-entering the code.
*#639# - This brings you to the menu which just re-programs your phone faster. I wouldn't reccomend you doing this if you value your phone.
*#7780# - This takes you to a menu which says "Restore Factory Settings", i think you understand what will happen if you press yes :p
GSM Code:
This is the only GSM code i know from the top of my head, just search around for more as i'm sure they're out there.
*#0000# - This is probably the most useless code you can find, but anyway it just gives you information on when your phone was activated. If your phone was sent in for repair, then this date will have changed to the date when it was fixed.
To check the IMEI (International Mobile Equipment Identity) Type-
*#06#
Information you get from the IMEI-
XXXXXX XX XXXXXX X
TAC FAC SNR SP
TAC = Type approval code
FAC = Final assembly code
SNR = Serial number
SP = Spare
That code works not only on Nokia phones, but on ALL mobile phoens.
To check the phones Software revision type-
*#0000#
Information you get from the Software revision-
V 05.31
18-02-99
NSE-3
1ST Line = Software revision
2ND Line = The date of the software release
3RD Line = Phone type
To enter the service menu type-
*#92702689# (*#WAR0ANTY#)
Serial number (IMEI)
Production date (MM/YY)
Purchase date (MM/YY) You can only enter the date once.
Date of last repair (0000=No repair)
Transfer user data to another Nokia phone via Infra-Red
Clock Stopping
To check weather your SIM Card supports clock stopping type-
*#746025625# (*#SIM0CLOCK#)
Revealing the Headphone and Car-Kit menus
Please note that if you do these next tricks, the new menus can't be erased without retoring the factory default settings. To do these tricks you need to short-circuit the pins on the bottom of the phone next to where you plug in you charger.
1. To activate the "Headset" menu, you need to short-circuit pins "3" and "4". After a short time the word "Headset" will be shown in the display. Menu 3-6 is now enabled.
2. To activate the "Car" menu, you need to short-circuit pins "4" and "5". After a short time the word "Car" will be shown in the display. Menu 3-7 is now enabled.
THE REBOOT TRICK
This should work on all software versions of the 6110.
1. Go to the Calendar (Menu-8)
2. Make a note or reminder.
3. Enter some text into the edit box.
4. Hold "Clear" until the whole text is cleared, then press "Back".
5. Press "0". The main screen will now be showing but a space appears on the screen. (you can't see it)
6. Enter 4 digits (e.g. 1234).
7. Use the down arrow to move the cursor to the left side of the numbers and the space (Down arrow twice).
8. Now enter 6 digits and press the call button.
Wait for a few seconds, the screen should start to flash and reboots. It should alsowork on other menus like the "Profiles" menu.
EFR CALL QUALITY
To activate EFR (Enhanced Full Rate) Enter the code-
*3370#
This improves call quality but decreases batterylife by about 5%
To deactivate it, Enter the code-
#3370#
THE JAMES BOND TRICK
If you short-circuit theleft middle and right pins on the bottom of the phone with all connections touching each other, the Nokia software hangs! The profile "Headset" will be activated. Before you do this just activate the "Automatic Answer" in the headset profile and set the ringing volume to "Mute". Now you can use your phone for checking out what people are talking about in a room. Just place it under a table in a room and call it. The phone receives the call without ringing and you can listen to what people are saying.
NETWORK MONITOR
There is a hidden menu inside your Nokia phone. If you want to activate it, you'll have to re-program some chips inside of your phone.
Check your software version. You can only continue if you have v4.33, v4.73 or v5.24.
Take apart the phone.
De-solder the EEPROM (ATMEL AT 24C64).
Read out the data with an EEPROM programmer and save it to a file (Backup).
If you have v.33 or v4.73, change the address "03B8" from "00" to "FF".
If you have v5.24 then change the address "0378" from "00" to "FF".
Write the new data to the EEPROM and solder it back to the phone,
Power on your phone and you should have "Netmonitor" enabled.
The Network Monitor gives you the following information.
Carrier number
MS RX Level in DBM
Received signal quality
MS TX power level
C1 (Path loss criterion, used for cell selection and reselection). The range is -99 to 99.
RTL (Radio link timeout).
Timeslot
Indication of the transmitter status
Information on the Network parameters.
TMSI (Temporary Mobile Subscriber Identity).
Cell identification (Cell ID, Number of cells being used).
MCC (Mobile country code)
MCN (Mobile network code)
LAC (Location area code)
Ciphering (On/Off)
Hopping (On/Off)
DTX (On/Off)
Discard cell barred information
CHECK SIM-LOCK
Note - If you bought your Nokia on UK Vodafone or UK Cellnet you do not need to check this because they both transmit on GSM900, and they don't lock the phones. However if you bought your phone on UK Orange or UK One2one your phone may be blocked. The reason is that they both transmitt on GSM1800. To make a call on GSM1800 you need what is known as a "Dual band" phone. A dual band phone is able to transmit on both GSM900 and GSM1800, so they lock the phones so you can't use it with any other network simcard. If you find that your phone is locked you can try different software to unlock it. (we havn't found one that works yet), or you can ask your service provider who will gladly exchange the 10 digit code for about £35.
This is how to check the status of the 4 different locks. Aslo don't try entering the wrong number, because after 3 times it will block the phone for good.
There are 4 different locks on your Nokia phone.
COUNTRY-LOCK
NETWORK-LOCK
PROVIDER-LOCK
SIMCARD-LOCK
The code to read out the sim-lock status of your phone is
#PW+(MASTERCODE)+(Y)#
# = DOUBLE-CROSS
W = PRESS "*" THREE TIMES
P = PRESS "*" FOUR TIMES
+ = PRESS "*" TWO TIMES
MASTERCODE = 1234567890
Y = NUMBER 1 TO 4
The master code is a secret code. The code has 10 digits, To read out the sim-lock status you can enter every combination you want!
"Y" Shows the status of the network-lock. Here you can enter a number from "1" to "4". The "4" is for the sim-card lock.
SIM-LOCK CHECKS
#PW+1234567890+1# = GIVES PROVIDER-LOCK STATUS
#PW+1234567890+2# = GIVES NETWORK-LOCK STATUS
#PW+1234567890+3# = GIVES COUNTRY-LOCK STATUS
#PW+1234567890+4# = GIVES SIM-CARD-LOCK STATUS.
You need a PC or a Laptop and the required connectivity tools ,ie.,
Serial/USB cable OR Infrared Device OR Bluetooth dongle
1) Activate Airtel Live! ( It’s FREE so no probs)
2) Create TWO Airtel gprs data accounts (yep TWO) and select the
FIRST as the active profile.
3) Connect your mobile to the PC (or Laptop) and install the driver for
your mobile’s modem.
4) Create a new dial-up connection using the NEW CONNECTION
WIZARD as follows
Connecting Device : Your mobile’s modem
ISP Name : Airtel (or anything you like)
Phone Number : *99***2#
Username and Password : blank
5) Configure your browser and download manager to use the proxy
100.1.200.99 and port 8080.( My advice is to use Opera since you
can browse both wap and regular websites)
6) Connect to the dial-up account. You will be connected at 115.2
kbps (but remember, that is a bad joke).
7) Pick up your mobile and try to access any site. You will get “Access
Denied…”(except for Airtel Live!). IT DOES NOT MATTER.
Keep the mobile down.
8 ) On the PC ( or Laptop) open your browser, enter any address ,
press ENTER and…….WAIT
9) After a few seconds the page will start to load and you have the
WHOLE internet at your disposal. ***************************************************************************************************************
TWO
Under DATA COMM
~~~~~~~~~~~~
APN : airtelfun.com
USERNAME : blank
PASSWORD : blank
PASS REQ : OFF
ALLOW CALLS : AUTOMATIC
IPADDRESS :
DNSADDRESS :
DATA COMP : OFF
HEADER COMP : OFF
Under INTERNET PROFILES
~~~~~~~~~~~~~~~~
INTERNET MODE : HTTP or WAP (both worked for me)
USE PROXY : YES
IP ADDRESS : 100.1.200.99
PORT : 8080
USERNAME :
PASSWORD :
No Risk Here, Try it and Enjoy
alternate
For All Airtel Users
Requirements:
1. Airtel live (available 4 free)
2. Nokia series60 handset e.g. 6600,6630,n series,7610,6670 etc
3. Opera wap browser 4 mobile
Procedure:-
1. Go to your connection settings and make a new internet profile using the default settings of airtel live. name that new profile as anything (for e.g. masala); change the home page of that profile to anything u like for e.g. www.google.com
2. Go to your Opera browser and set the default connection as AIRTEL LIVE. this is the original settings u received thru airtel.
3. Go to the services (in N6600) and Web (N6630) and change the default profile for connection as masala (newer one).
**Note: always make sure that your access point is airtelfun.com
Apply:-
1. Open Opera and u will see that homepage of Airtel Live is opened. Minimize the application.
2. Now open web using the duplicate Profile and u will see that two Gprs connections will work simultaneously and at the web or the services page it will show "Unable to connect" or any error. well that's the signal of your success.
3. Simply go on the Opera with web on and open any site u want for free. No Charges No nothing.
U can also use it through your computer..........
BSNL hack for Internet
Free Gprs in bsnl
here are the steps to perform:-
Logic: the server has a major bug in it, by which it fails to block two simultaneous connections from the phone and establishes a connection with full internet working,
Supported devices: all phones with multi channel Gprs support
For connection on your mobile phone:-
1) Make two connections like bsnlportal and BSNLPORTAL1
(names of profile don’t matter, u can keep one as billgates and shahrukhkhan lol..the basic purpose of names is to enable the user to differentiate between the two accounts,)
2) Select the application you got to have the full connection working on.
Surpassingly “web” now just select “bsnlportal” profile and select a link like wap.cellone.in the page will get open, just press the red button such that the “web” application goes in the background.
Make sure that the gprs connection is still established with the web app. Two parallel lines on the top left of the screen will confirm this
3) Now open any other app that requires web connection like opera. Select BSNLPORTAL and open any other link like wap.google.com, u will get error –
the aim of using the other app is to perform multi-channel gprs,
this is verified by seeing some dots on the pre-existing connection established by “web”
(step 2)
“Access denied.
Technical description:
403 Forbidden - You are not allowed to communicate with the requested resource.”
4) close opera and open web and open a site like esato.com
5) if everything is done as said here then esato will load and voila! We have the whole internet!
For connection on pc.
1)create a connection and enter the number to be dialed as *99***1#
2) enter the following string as extra initialization command
3)now dial from pc, the connection will be established
4)pick the phone and open “web” open “wap.cellone.in” the phone shows error .
5) close “web” and then from the browser open www.google.com
and voila! The whole intenet is here
settings for profiles
apn: celloneportal
ip: 192.168.51.163
port : 8080
leave other fields blank as they are of the least concern!
the browser settings on pc too go the same as mentioned above!
 Fring is a life saving mobile application which allows us to make free calls, send messages to other Fring user and PC-based VoIP services such as Skype and Google Talk. Fring doesn’t cost any airtime because it’s patented P2P Mobile VoIP technology sends voice calls over GPRS, 3G or Wi-Fi. It can also make landline calls using your SkypeOut credits.
Fring is a life saving mobile application which allows us to make free calls, send messages to other Fring user and PC-based VoIP services such as Skype and Google Talk. Fring doesn’t cost any airtime because it’s patented P2P Mobile VoIP technology sends voice calls over GPRS, 3G or Wi-Fi. It can also make landline calls using your SkypeOut credits.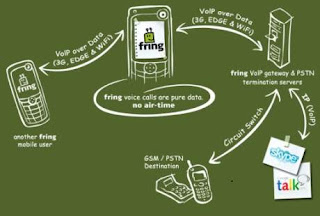
You can call anybody on your Skype, Google Talk contact list for free, they can call you as well. Isn’t it a life saver?
I’ve tried Fring from both the ends, voice quality is fairly good, but the voice gets choppy inside buildings or basements (I guess, that’s quite natural). To get Fring, go to their download page and fill-in some details, you’ll get a text containing the download link. As of now, Fring supports only Nokia handsets including N70, N72, N80, N80i, N90, 6630, 6680, 6681, 6682. Fring Fring!
Tip 1 :Do u know how to use the edit button (abc or pencil button)?Heres how... in the inbox for example; u wanna delete multiple sms, simply hold the edit button, scroll down, and then, press c to delete the marked sms. The edit button can also b used to copy and past text in sms, simply hold it and scroll across, choose copy. pretty good for placing song names in ngage.
Tip 2:Shit happens,on a smartphone,its inevitable u do something wrong,and tis calls for a format of fone. to format the fone, press *#7370#, then enter the lock code, which is the sec code of the fone.
NOTE: batt must b full, else if format is disrupted by low batt, consequences will b disastrous.I heard the code *#7780# works too, pretty much the same i think.
for 6600 users, to format the fone, theres an alternative way. Press and hold <3>, <*>, and the buttons,then power on fone, keep holding on the 3 buttons, till u come to a format screen. tis method ONLY works on 6600, and need not enter the sec code. BUT sec code wud be reset to default 12345.
Tip3:TO NGAGE USERS; Did u know u can install .sis files simply using the cable given? Juz plug it in, place the .sis file anywhere on e:(the mmc), not in any folders, root of e:,disconnect,then look for it in manager.
Tip 4:Save memory when installing apps, by installing over bluetooth. This can be done using the nokia phone suite and a bluetooth serial connection. Only works with .SIS files, so java still has to be sent to the phone, but will save space when using .SIS files.
Motorola Secret Codes
Motorola
IMEI number:
*#06#
Code to lock keys. Press together *7
Note: [] (pause) means the * key held in until box appears.
Select phone line - (use this to write things below the provider name):
[] [] [] 0 0 8 [] 1 []
Add phonebook to main menu:
[] [] [] 1 0 5 [] 1 []
Add messages to main menu:
[] [] [] 1 0 7 [] 1 []
Copy SIM memory (phonebook menu):
[] [] [] 1 0 8 [] 1 []
Eng Field options (main menu):
[] [] [] 1 1 3 [] 1 []
Slow (Frequency of search menu):
[] [] [] 1 0 1 [] 1 []
Medium (Frequency of search menu):
[] [] [] 1 0 2 [] 1 []
Fast (Frequency of search menu):
[] [] [] 1 0 3 [] 1 []
Enable EFR:
[] [] [] 1 1 9 [] 1 []
Function :
[] [] [] # # # [] 1 []
Change pin:
[] [] [] 0 0 4 [] 1 []
Unblocking using the "puk" number:
[] [] [] 0 0 5 [] 1 []
There are lots of similar codes exist. If you change the last number to 0 you can deactive that code. The 3 digit number at the middle are from 0 to 999. I put the most interesting codes. (EFR):Enhanced Full Rate Codec.
You can change GSM frequencies to 900/1800 by entering the enginnering model. Following the below steps:
enter menu and press 048263* quickly, then you will enter the secret engineering menu
under "Opcode"
input 10*0*3 for GSM 900
10*0*4 for GSM 1800
10*0*5 for GSM 1900
10*0*6 for dual band GSM 900/1800
10*0*7 for dual band GSM 850/1900
To add extra message space 4 your Motorola C350 C450 C550 or C650, press menu button, press 048263* quickly, then on the popup menu enter 47 press ok.press 50 and ok.press 1 ok.press 64 ok.press 1 ok.press 186 and ok.You will receive an extra 50 msgs memory space.Switch phone off and back on.(not tested)
Important!
Try these codes at your own risk! We don't accept any complaints.

